Which of the Following Best Describes Residual Risk
The level of risk after security measures are applied D. Residual Risk Threats x Exploit x Asset Value x Control Gap.

Ppm Glossary What Is Risk Management
The categorization after implementation of mitigating actions.

. Organizations identification and analysis of the risks that threaten the. Enterprise risk management is narrower than internal control and focuses on risk mitigation strategies across the enterprise. An inherent risk is the probability or likelihood of a risk occurring multiplied by the impact should it actually occur.
Total risk asset value countermeasures residual risk. Residual risk is the level of risk after security measures have been applied. The likelihood of occurrence of a threat B.
Moreover the same risk can be utilized by two individuals in different ways. The categorization after mitigation and residual risk assessment D. SLE frequency ALE which is equal to residual risk C.
The impact of risk if a threat is realized. How long before an investment will pay for itself. The usefulness of the risk to individuals or groups.
The level of risk after security measures are applied D. Which of the following shows how devices are connected and includes an IP allocation register. An analytical method that simulates a real-life system for risk analysis.
Independent outside auditors assessment of residual risk. The categorization after initial risk assessment D. Management should act to reduce risks to the lowest possible.
Which of the following best describes the meaning of Initial Level of Risk in Risk Management. The risk assessment component of internal control involves the. Which of the following best describes the meaning of Initial Level of Risk in Risk Management.
Which of the following relations correctly describes residual risk. The categorization after initial risk assessment C. Risk treatment is an iterative process.
An inherent risk can be defined as the difference between the risk response benefit and the residual risk produced by the particular risk response. The utility of the risk describes the usefulness of a particular risk to an individual. Which of the following best describes a Monte Carlo simulation.
December 14 2021 When residual risk is minimized. The impact of risk if a threat is realized Answer. The categorization after mitigation and residual risk assessment E.
The impact of risk if a threat is realized. The categorization after implementation of mitigating actions B. The categorization before risk identification.
Threats vulnerability asset value control gap residual risk D. Which of the following best describes the meaning of Initial Level of Risk in Risk Management. It is considered a form of internal control The competition probably has one To comply with the securities and exchange commission To follow the DATA act.
Which of the following should George use to calculate the companys residual risk. An analytical method that simulates a real-life system for risk analysis. Risk that cannot be mitigated Risks that if properly managed will make the organization successful in the achievement of its objectives or if not well managed it the organization will not achieve its objectives A component of overall audit risk None of the above describes residual risk QUESTION 8.
The categorization after implementation of mitigating actions. Which of the following best describes residual risk. Internal audit functions assessment of control deficiencies.
Management should treat risks at least annually. This preview shows page 16 - 19 out of 36 pages. The level of risk before security measures are applied is the inherent risk.
The level of risk before security measures are applied C. After treatment the inherent risk results in the residual risk which needs to be treated after another round of risk assessment if it is not acceptable. The categorization after initial risk assessment C.
Which of the following statements best describes the principle of ALARP. Which of the following best describes residual risk. The level of risk before security measures are applied C.
Threats vulnerability asset value residual risk B. Which of the following best describes ROI. The likelihood of occurrence of a threat B.
The level of risk before security measures are applied C. Enterprise risk management is narrower than internal control and focuses on managing the risk of loss resulting from external events. Which of the following is true of an inherent risk.
The categorization after implementation of mitigating actions C. Management should act to lower risk until the costs of further treatment. Residual Risk Threats x Vulnerability x Asset Gap x Control Gap.
Which of the following best describes a Monte Carlo simulation. Which of the following BEST demonstrates to an IS auditor that an organization has implemented effective risk management processes. Total risk asset value countermeasures residual risk.
Which of the following definitions best describes enterprise risk management. Which best defines residual risk. Threats vulnerability asset value residual risk B.
Which best defines residual risk. Which of the following should George use to calculate the companys residual risk. Management should treat risks until the residual risk equals the inherent risk.
Which of the following best describes why companies should establish a written code of ethic. December 21 2021 What happens when you attempt to compile and run the following code. Residual Risk Threats x Vulnerability x Asset Value x Control Gap.
The level of risk after security measures are applied D. Which of the following best describes the meaning of Initial Level of Risk in Risk Management. The categorization after initial risk assessment C.
What best describes residual risk. Threats vulnerability asset value controls gap residual risk D. Residual Risk Threats x Exploit x Asset Value x Control Gap.
Financial outcomes are one of the methods for measuring potential value for taking a risk. SLE frequency ALE which is equal to residual risk C. Residual risk is the risk after treatment.

Risk Acceptance Criterion An Overview Sciencedirect Topics

Residual Risk Calculation Igrafx Platform 17 8
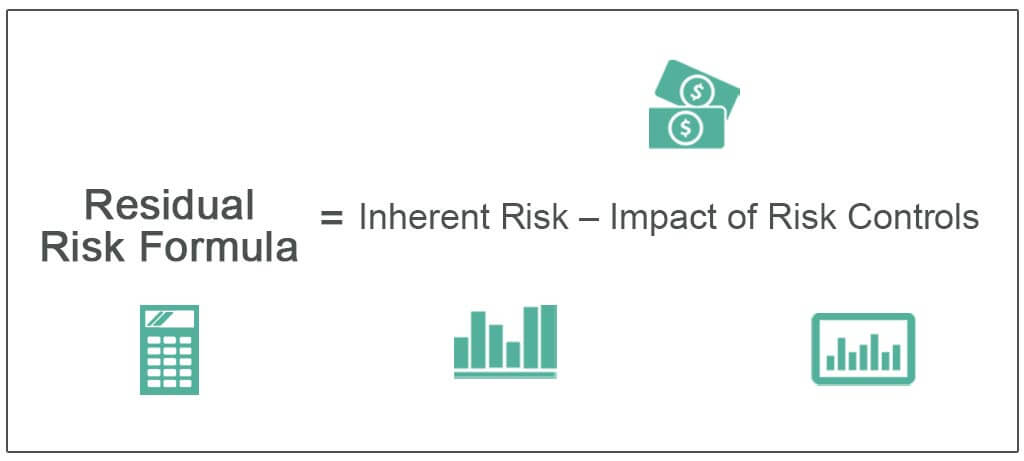
Residual Risk Examples How To Calculate Residul Risk

Residual Risk Vs Secondary Risk Pmp Concepts Simplilearn

Pin On Solutions All Academics

Residual Risk Computation Download Table

Risk Tolerance An Overview Sciencedirect Topics
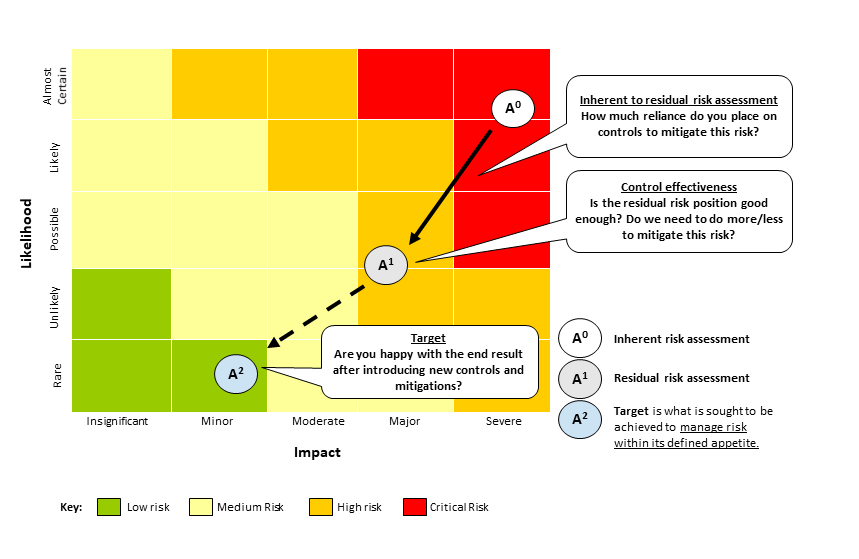
Ict Risk Management Guidance Nz Digital Government
Inherent Risk Vs Residual Risk Explained In 90 Seconds
Inherent Risk Vs Residual Risk Explained In 90 Seconds
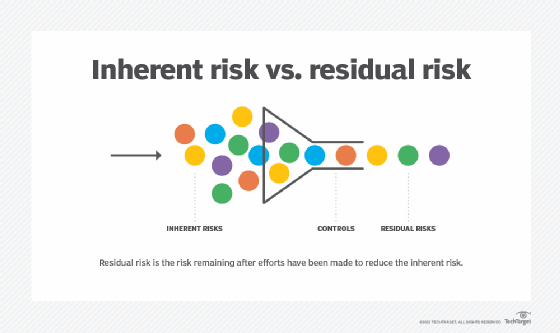
What Is Residual Risk How Is It Different From Inherent Risk

Project Risk Management Plan A Short Guide Projectcubicle Project Risk Management Risk Management Strategies Risk Management Plan

Inherent Risk Vs Residual Risk Explained In 90 Seconds

Residual Risk Computation Download Table

Class 21 Poisson Regression Intro Model And Example In 2021 Regression Intro Poisson Distribution

A System To Calculate Cyber Value At Risk Sciencedirect


Comments
Post a Comment